Well if you don’t know about Apple’s Safari 3 Launched for Windows, then first start its download as its worth giving a try!
Being a fan of Apples product line I was delighted by Safaris availability on Windows platform. The features I really like is its kool built-in RSS feed reader! As of now I can safely say that its my second favorite browser next to Firefox (yes nothing seems to beat firefox) 🙂
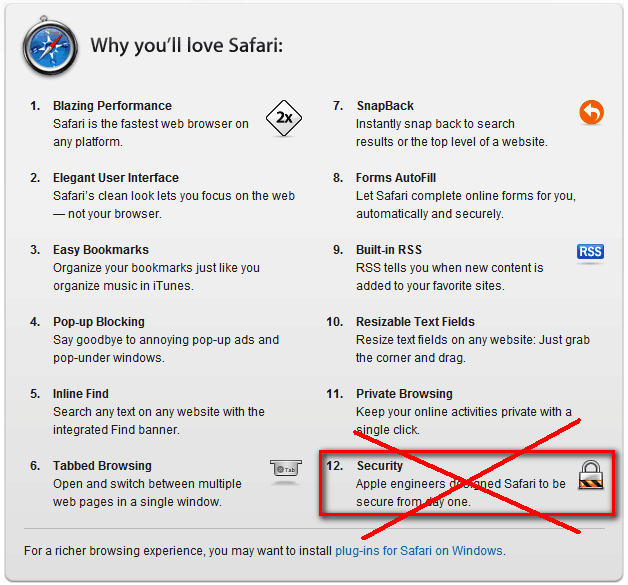
Though Apple described 12 reasons on their site their security claimed was zeroed in 2 hours of Safaris release!
The credit goes to Thor Larholm, who wrotes in his post Safari for Windows, 0day exploit in 2 hours
…. The logic behind this vulnerability is quite simple and the vulnerability class has been known and understood for years, namely that of protocol handler command injection. A browser typically consists of a multitude of different URL schemes, some of which are handled by internal functions and others that are handed off to external applications. On the OS X platform Apple has enjoyed the same luxury and the same curse as Internet Explorer has had on the Windows platform, namely intimate operating system knowledge. The integration with the originally intended operating system is tightly defined, but the breadth of knowledge is crippled when the software is released on other systems and mistakes and mishaps occur…
URL protocol handlers on the Windows platform work by executing a process with specific command line arguments. When Apple released Safari for the Windows platform they neglected to implement a proper level of input validation for these arguments, which means that you can break out of the intended confines and wreak havoc….
He has described step by step method to use (or abuse) this exploit!
Finally its proved again that nothing is safe on Windows… 😉
You must be logged in to post a comment.